Netcat 101: Remote Shells From Windows into Linux, HakTip 87
Hak5 — Cyber Security Education, Inspiration, News & Community since 2005:
____________________________________________
This week on HakTip Shannon is connecting to linux from windows with Netcat!
Welcome to HakTip — the show where we breakdown concepts, tools and techniques for hackers, gurus and IT ninjas. I’m Shannon Morse and today I’m creating remote shells with Netcat in Linux!
Remote shells on Linux are similar to Windows. When you begin, you’ll notice no user prompt appears for you. You also need to run Netcat through sudo to do remote shells (super user).
This time, the listener is my Linux machine, so we will start there with this command: sudo nc -lp 31337 -e /bin/bash
This will start Netcat under super user control (or root), and open a persistant listening port on 31337, while pulling up /bin/bash (which is basically the equivalent of Windows command prompt.
Now on your Windows box, you can connect to the host PC and that opened port. The listener (my Linux machine) will give bash to my Windows PC. The command for this is: nc 192.168.0.32 31337We’re connected! It does look a little different than the Windows version,.
Now we’ll start toying around with some features of a remote shell on Linux. I’ve got both of my computers set up and connected, so now I’m going to type ls on my Windows command line to see a return listing of directories on my Linux machine.
Now let’s make a directory on the Linux machine. In Windows I can use mkdir MyDirectory. We can use the ls command again to see if the directory was indeed created. Now let’s add a new user and give them root access. The command is: useradd -g root NewName
Now I can use this command to make sure that user has been created: grep NewName /etc/passwd
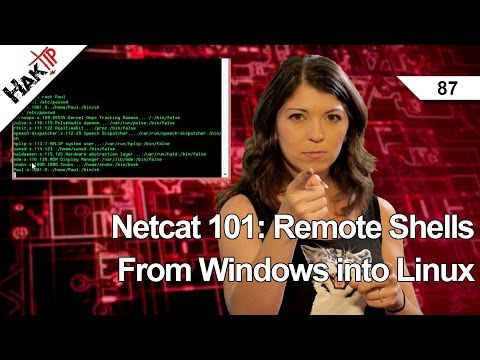
Now I’m going to dump the entire /etc/passwd file using: tail /etc/passwd
Do you use Netcat? Send me a comment below or email us at [email protected].
And be sure to check out our sister show, Hak5 for more great stuff just like this. I’ll be there, reminding you to trust your technolust.
-~-~~-~~~-~~-~-
Please watch: “Bash Bunny Primer – Hak5 2225”
https://www.youtube.com/watch?v=8j6hrjSrJaM
-~-~~-~~~-~~-~-
____________________________________________
Founded in 2005, Hak5’s mission is to advance the InfoSec industry. We do this through our award winning educational podcasts, leading pentest gear, and inclusive community – where all hackers belong.
Comments are closed.