Apache Tomcat – CGIServlet enableCmdLineArguments RCE Demo by Safe Security | CVE-2019-0232
🔥HACK POC OF THE WEEK [11-MAY-2022]🔥
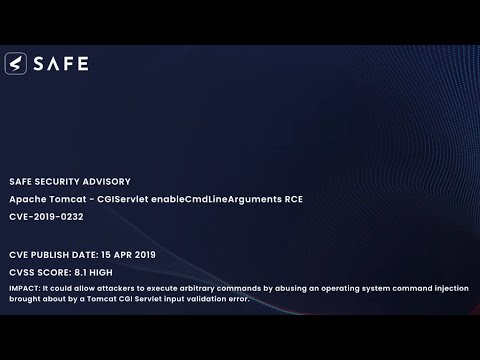
CVE-2019-0232: Apache Tomcat – CGIServlet enableCmdLineArguments RCE Demo by Safe Security
Summary: Apache Tomcat is an open-source application server that implements the Java Servlet and Java Server Pages (JSP) specifications, providing an environment for Java code to run.
RCE Exploit: It could allow attackers to execute arbitrary commands by abusing an operating system command injection brought about by a Tomcat CGI Servlet input validation error.
Mitigation
————
1. Disable CGI support (it is disabled by default).
2. Users should set the CGI Servlet initialization parameter enableCmdLineArguments to false to prevent possible exploitation of CVE-2019-0232.
3.Apache implemented “regex” pattern [[a-zA-Z0-9Q-_.\/:E]+] to prevent input from executing as commands on Windows systems.
For the SAFE Platform Demo visit: https://lnkd.in/dNZazYi
#hacking #hackoftheweek #safesecurity #thirdpartyriskmanagement #cisos #cios #ciso #cio #infosec #cybersecurity #cyberawareness #security #windows #java #exploit #livedemo
Comments are closed.