Shoryuken – SQL Injection Takeover Tool (MySQL & MSSQL)
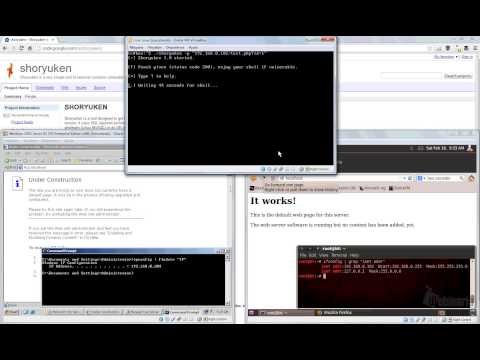
Shoryuken is a very simple tool to takeover systems vulnerable to SQL injections. It runs from bash (linux) and only needs curl installed.
It can be used to pwn a Linux system with MySQL or a Windows machine with MSSQL.
In this video, it is used against 2 systems in a internal virtual network:
1) Windows 2003 Server R2 SP2 with IIS 6.0 + MSSQL 2005
2) Backtrack r2 3.2.6 with Apache 2.2.14 + MySQL 5.1.41
Both are serving pages vulnerable to SQLi with:
1) DB user ‘sa’ running as SYSTEM
2) DB user ‘root’ running as ROOT
The takeover is pretty straightforward using a single request to open a “custom shell”:
1) xp_cmdshell output redirected to a file at web server root (c:inetpubwwwroot)
2) PHP one line web shell with sudo at web server root (/var/www)
These techniques have the following advantages:
– Don’t need to download/upload anything to target
– Don’t need an extra open port on system
– Don’t need an extra open port on network firewall
More info & download: http://code.google.com/p/shoryuken/
See also for demonstration of MySQL technique:
A Brute Pwn – Rooting a Box via SQLi when MySQL Runs as Root
http://www.youtube.com/watch?v=5dcjLPaE5qI
Don’t learn to HACK, hack to LEARN.
http://about.me/brutelogic