XSS Vulnerability in Google Sandbox Domain via SVG File Upload | Google XSS – Cross Site Script Bug.
Welcome Youtubers !!!
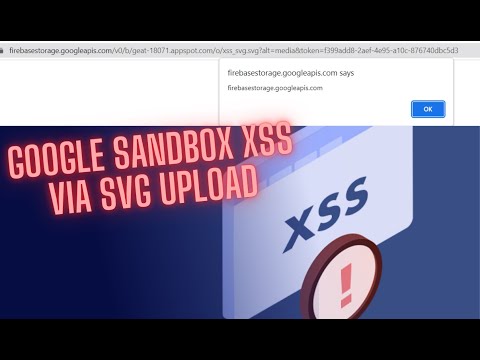
The author of the provided information has discovered a Cross-Site Scripting (XSS) vulnerability in the Google sandbox domain “https://firebasestorage.googleapis.com/” by uploading an SVG file. While Google sandbox domains are generally immune to external impacts, this discovery is purely for educational purposes.
Exploiting XSS vulnerabilities can allow attackers to inject malicious code into a web page, which can then execute in the context of an unsuspecting user’s web browser. This can result in the theft of sensitive user data or the execution of unauthorized actions on behalf of the user.
In this particular case, the author has found that uploading an SVG file can trigger an XSS vulnerability in the Google sandbox domain. The details of how this exploit works are provided, but it appears to be related to the way SVG files are parsed and rendered by the browser.
https://instagram.com/dead_______deal
#XSSvulnerability #GoogleSandboxDomain #SecurityVulnerability #SVGfile #ProofOfConcept #ResponsibleDisclosure #EthicalHacking #WebSecurity #InformationSecurity #Cybersecurity #OnlineSecurity #WebVulnerabilities #HackingEducation #google #bug